SkyDog 1 VM Walkthrough
for the SkyDog 1 VM hosted on Vulnhub from James Bower.
I liked the 2016 Skydog which I did a walkthrough for already, and here I’d found that the author of that had also done another; Skydog 1, so I thought I’d give it a shot.
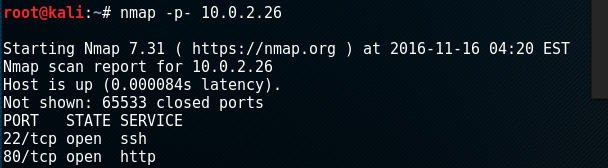
First off, nmap found the following ports open:
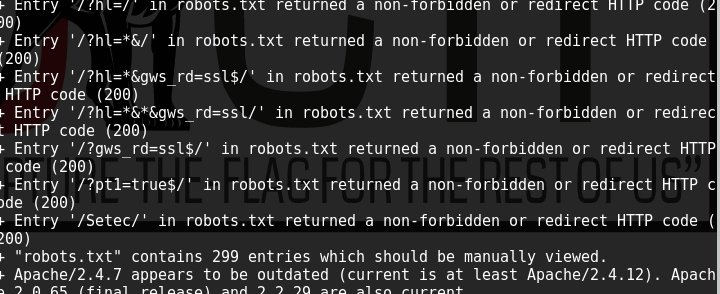
Running nikto on port 80 finds some useful directories and the presence of robots.txt
I visit the http content through the browser which is a static page with the logo shown at the top of this post.
Flag #1 Home Sweet Home or (A Picture is Worth a Thousand Words)
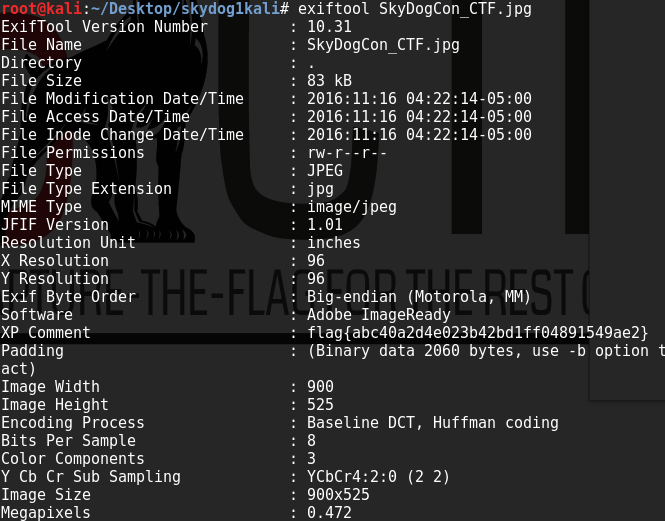
Since the home page pretty much only contains that image, I ran it through exiftool to find the first flag
this decrypts to “Welcome Home”
Flag #2 When do Androids Learn to Walk?
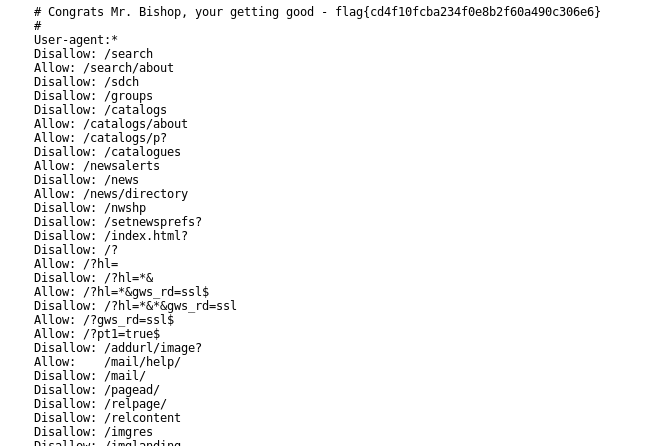
This was a great pun I liked, referring to robots.txt for crawling :) Nikto had already put this on our radar earlier, so time to take a look:
Flag #3 Who Can You Trust?
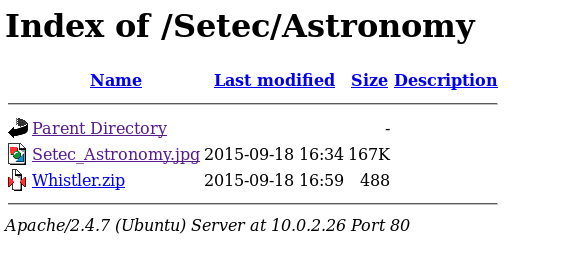
Another thing nikto showed us earlier was that although most of the entries in robot.txt don’t exist on the server, the Setec directory does, so we navigate there. It contains an image but no exif data this time, but it’s stored on an Astronomy subdirectory, so I navigate there too and find a directory listing:
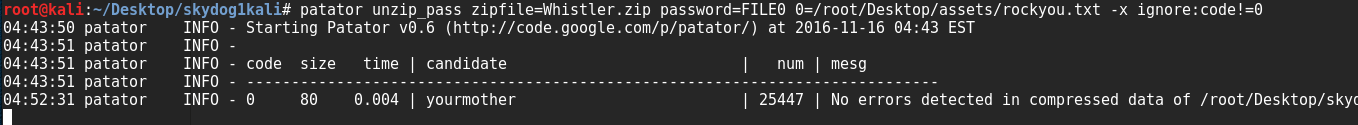
We can see there is a zip file here, so we download that but it is password-protected. Running it through patator with the rockyou.txt password list we find that the password is yourmother.
This contains another flag.
Flag #4 Who Doesn’t Love a Good Cocktail Party?
The other file in the zip is Questttofindcosmo.txt:
Time to break out those binoculars and start doing some OSINT
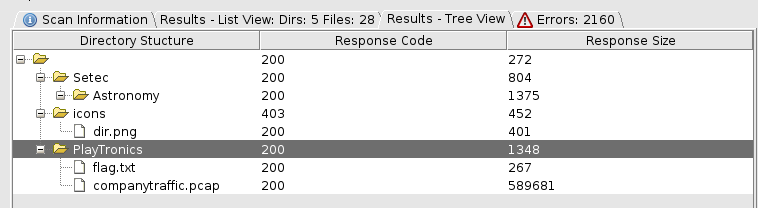
We find out the images, Cosmo etc is a reference to a 1992 film “sneakers”, so I use the imdb page as an input to cewl to create a wordlist, which we feed into dirbuster.
Dirbuster has found another subdiretory. This finds another flag which decrypts to leroybrown.
Flag #5 Another Day at the Office
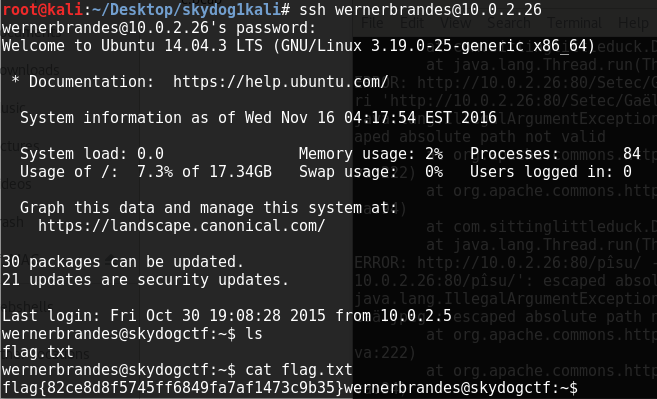
Another file in that subdirectory was companytraffic.pcap, which looks exactly what the clue alludes to, so we open it up in wireshark to view. Ther’s a lot of content but eventually we find an audio file, which when we export is a voiceprint file for Werner Brandes. We use this and the leroybrown flag from earlier as the password and ssh in.
Flag #6 Little Black Box
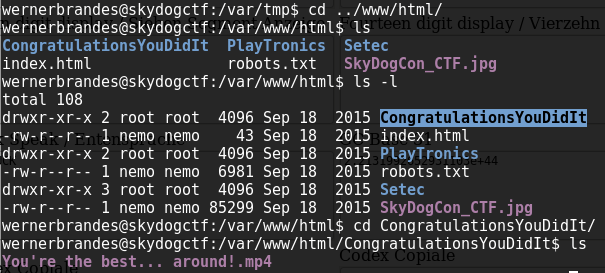
When I navigate to the /var/www/html directory to see if there was anything else useful in the web content I find a congratulations message:
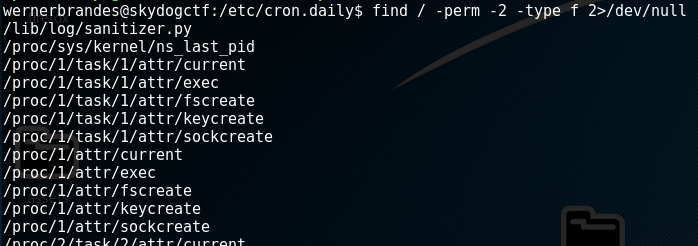
I suspect I’ve found this out of sequence though so continue to try and get root. One of the usual things I try at this stage is to search for world writeable files which shows an interesting python file:
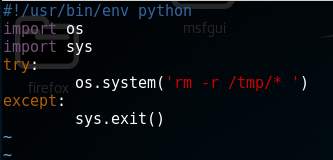
so we view the contents of this:
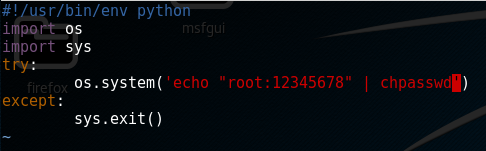
I change the contents to give me root access:
and then go and make a cup of tea, when I come back the cron job that calls it has run and i can view the last flag in the root directory:
So I did find that congratulations flag out of sequence, but it was still worth it to find root anyway!