OSCP Exam passed!
My experience at taking the OSCP PWK course
My Background
I work in Quality Assurance/automation and have a programming degree, so I’m comfortable within an IDE. I use OSX at work and Linux at home so I can work my way around a terminal. Before I started the OSCP course itself I spent around a year learning exclusively through vulnhub and hackthebox. Other than that I don’t have the traditional background many OSCP candidates have in network admin, having other certs etc. but I was confident I wouldn’t be too out of my depth.
My motivation was primarily personal interest, and a philosophy that security should be a concern from the very outset of a project, which as QA I am ideally-placed to implement.
Course prep
I first delved into penetration testing through Vulnhub. I would recommend this first due to the walkthroughs present for each box. It’s ok to have your hand held for a while to get the general process and pick up some tools (Even after I stopped using other walkthroughs and started contributing my own, I would still read through walkthroughs after finishing a box, just because of the many solutions different people can come up with to the same problem). After that I went to Hackthebox (Review here) which is much more competitive, and offers a lot more OSCP-style boxes (including vulnerable Windows hosts which aren’t available on vulnhub).
I didn’t really have a plan for the course other to enjoy myself and to both see how I measured up and to learn whatever I could (I think enjoying yourself is key to getting the most out of the course and will help you during the very stressful exam)
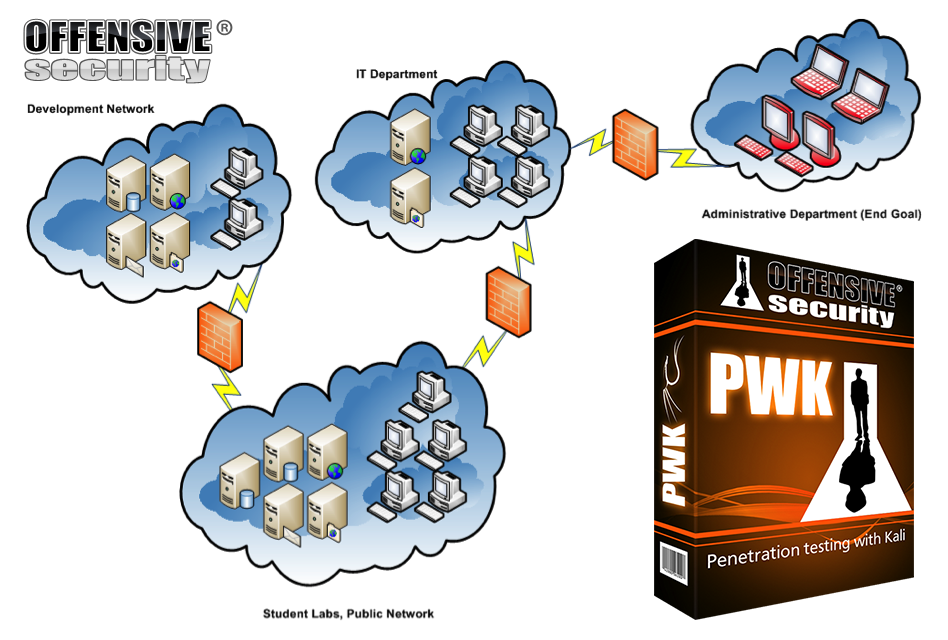
The labs
The best way to introduce the labs is with a brief overview and network map. The VPN represents a corporate network, made of many different operating systems, at different patch levels, with different running services with a variety of intended company uses and related misconfigurations.
“Users” are represented and may communicate with each other or work closely together, communicating over the network. It is up to you to asses this, map out the relationships and various job roles and make use of this to take control of firstly the public network, and then to pivot through this through firewalls onto other internal networks.
A lot of people will say to avoid metasploit during the lab time, but since I was doing it for fun I used it predominantly and had a good time, so I’d suggest to take your own counsel on however you feel like approaching the labs.
I work full-time and despite my best intentions sometimes I’d just go for a week or so without so much as logging in to the labs, but I don’t think doing something you enjoy should become a chore.
I booked 3 months in the labs with no aims or targets other than to take a test-run of the exam at the end of the second month and then use the remaining month to refine any areas that tripped me up. I had 38 machines for the lab rooted by the time I started the exam. I opted to forego the infamous machines like sufferance, pain etc as I felt the time could be better spent on a wider variety of boxes in preparation for the exam.
The Exam
The exam itself takes place over 24 hours, with the report due 24 hours after that. You are allowed to use metasploit only on one box out of the 5 you are assigned. The 5 boxes are given different amounts of points, but don’t make the mistake of assuming extreme relative levels of difficulty from that; They all take effort, and indeed I found some higher-level machines far easier than the lowest 10 point machine, so don’t get disheartened if you go for the 10 pointer straight away and find yourself coming up against a wall, just rotate to another box. Rather than set me at my ease for when I intended to take the exam for real, this time simply enforced it to me that this is so very arduous!
I got a root shell within 2 hours, but then after that there was a miserable 9 hours of absolutely no progress whatsoever. This even led me to firing my one metasploit chance at a carefully-chosen target and hitting absolutely nothing. Then firing every tediously-related exploit at every port and service on that box in a mad machine-gun spray and still nothing. But if you don’t lose your cool you’ll come out at the other end; at one point things just clicked and after around 19 hours I had 4 root shells and a user shell, I could’ve sought to escalate this last shell but I gave it up so that I could be rested for my report (I knew if I started it I’d get drawn into it..), so it’s comforting to know that metasploit isn’t essential for exam success.
The report came to just under 40 pages (I didn’t submit a lab/exercise report, which can net the candidate an extra 5%), and wasn’t text-heavy in the slightest; I recommend using the report template that offsec provide, it seems structured in a way to stop you being too verbose which saves time and effort. This combined with my background in QA meant I could basically write a concise yet informative test report in my sleep (Which was very nearly the situation at times!)
The result email came back to me very quickly which was a relief!
Thus far my plan is to spend my last month of labtime enjoying the labs stress-free and then going back to hackthebox, there are a lot of new boxes I’ve missed in the past two months.